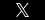Here’s a reminder about authenticating emails based on a posting from Prof. Colin Miller at EvidenceProfBlog. To paraphrase Prof. Miller:
And, like its federal counterpart, [Mil. R. Evid.] 901(b)(4) provides that
By way of illustration only, and not by way of limitation, the following are examples of authentication or identification conforming with the requirements of this rule:
 Court-Martial Trial Practice Blog
Court-Martial Trial Practice Blog